Mail Investigation Tool
The Mail Investigation Tool is an application developed by, Network Defense Solutions which can assist both end-users as well as SOC analysts in analyzing E-mail headers. The preface of the tool was mainly to establish a method for junior level analysts to more seasoned analysts to quickly obtain information from a threat actors E-Mail and incorporate the findings into a report, or assist in providing feedback regarding the origins or authenticity of an e-mail message.
E-Mail Analysis Features
- ThunderBird Header Analysis
- Outlook / O365 Header Analysis
- Apple Mail Header Analysis
- Gmail Header Analysis
- IOC Identification and Collection (E-mails, URL's, Domains, IP Addresses, Hashes)
- Domain Testing (Redirect detection)
- Whois lookup
- Virustotal URL generation
- Domain tools support (extended lookups)
- Spoofing Detection
- Text Analysis (Sender profiling)
- Google, Linkedin, Glassdoor and other OSINT Search capabilities
Initial Setup
The application does not require an installation application (msi, exe, etc.). You can simply drop the application in a directory and link to it or, call it from the main directory itself. The files within the directory must be present for other support (text analysis, etc.). Omission of those directories or configuration files may make the application itself unstable. If in the event there is a need for users to have an installation application built, please let us know!
Thunderbird E-mail Header Analysis
There are two methods you can utilize when attempting to analyze headers from thunderbird. You can simply drag the e-mail out of the main window as shown below:
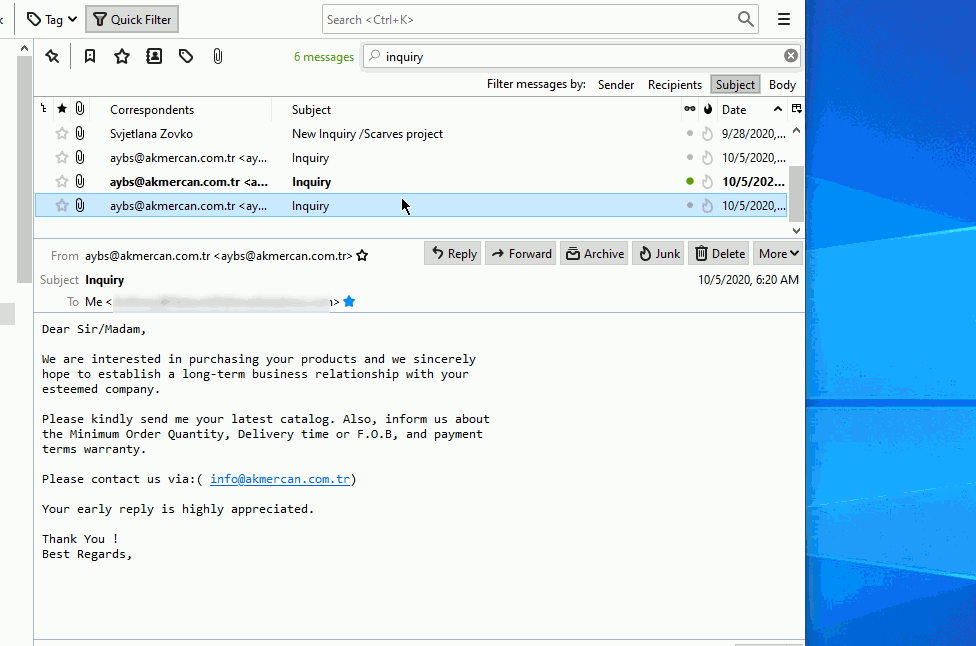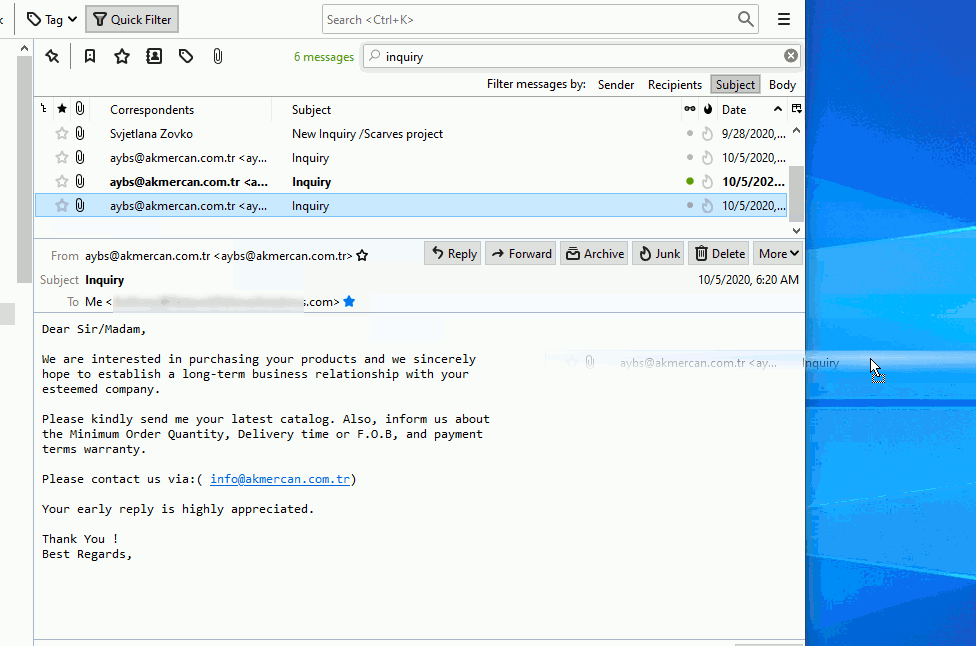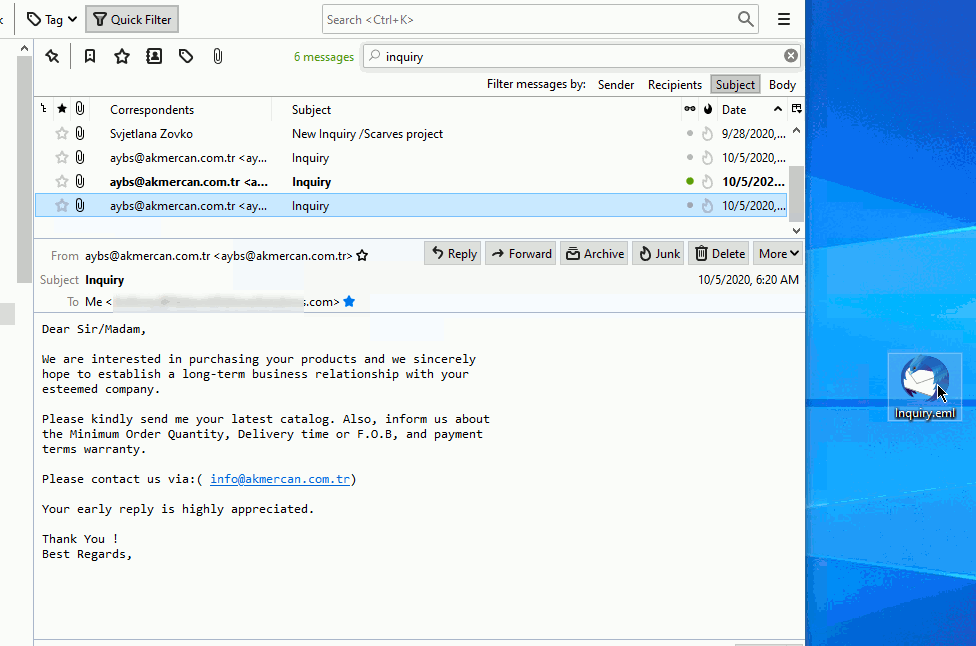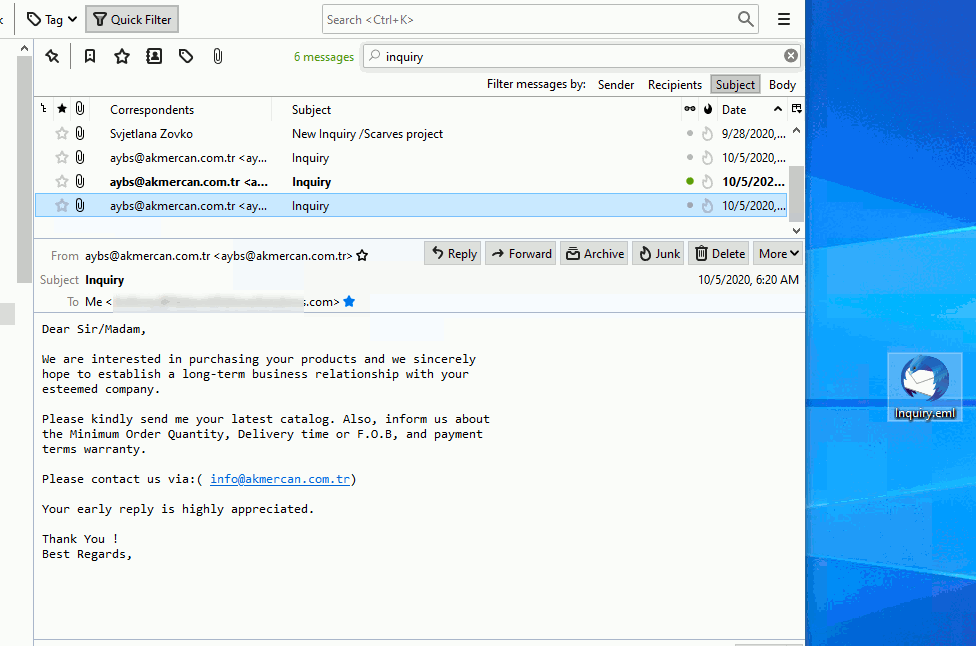
In the example we are using above, we are left-clicking the e-mail we want to remove from the e-mail client holding down on the left-click and dragging it out onto the desktop. Once this is completed, we have the e-mail to perform various tasks against. In our case, we will need to right-click the e-mail and then rename it to .txt as shown below:

Once we open the e-mail with notepad or, notepad++ we can then copy the correct contents from the e-mail into the application. We will cover this at a later time within this knowledgebase article
Another method that you can utilize in order to assist you with obtaining the e-mail header(s) is within the view menu as shown below:
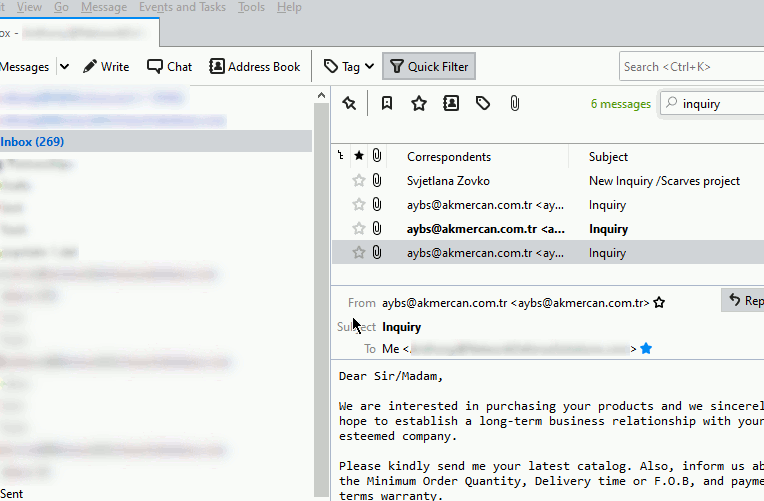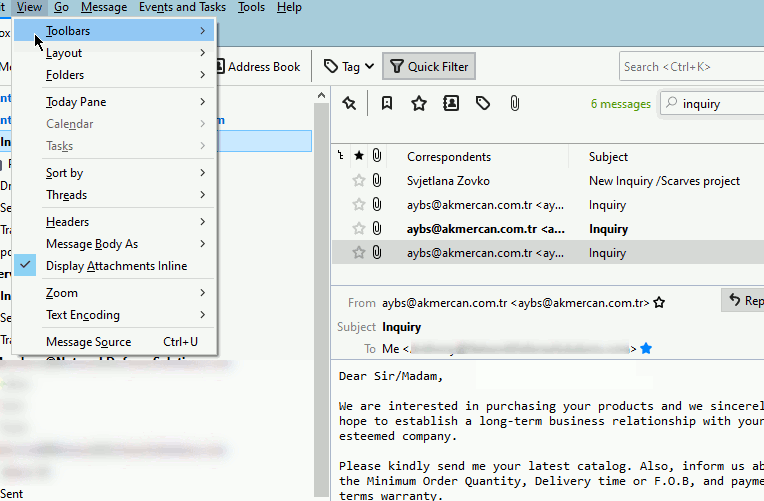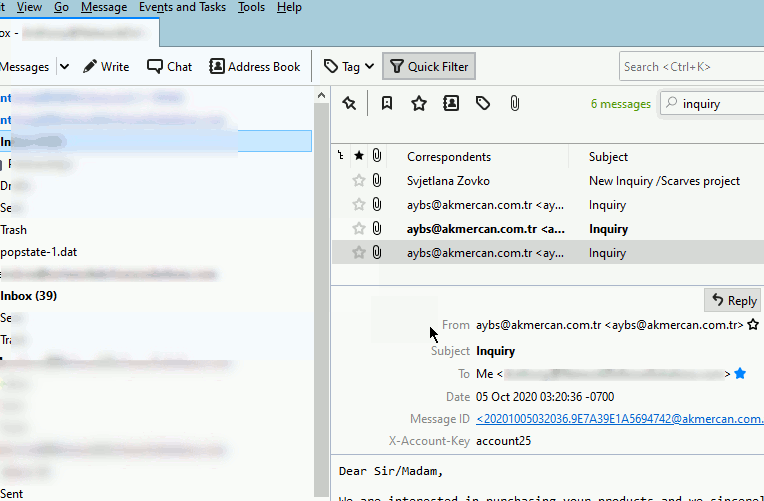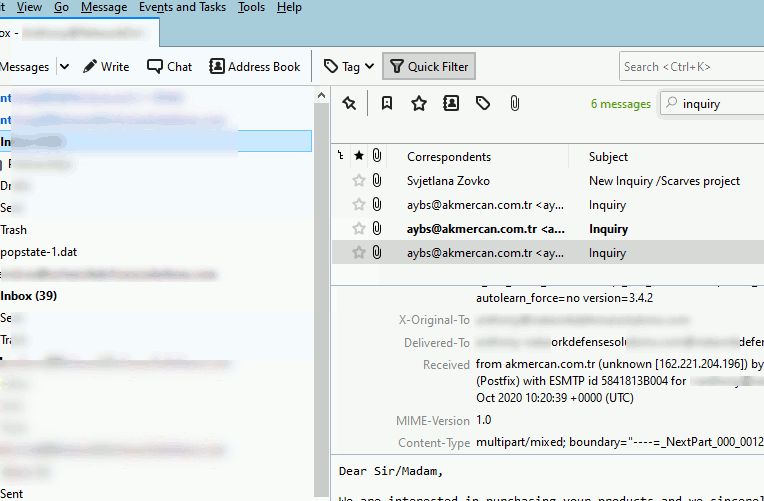
While the graphic does show you how to utilize the feature within Thunderbird, you can also go to View -> Headers -> All. Selecting "All" will display all the message headers on each e-mail that you receive.
Outlook & O365 Headers
Outlook headers are kind of, sort of simple to deal with as well, similar to the likes of Thunderbird. When a suspicious e-mail is received in outlook or the O365 suite you can follow these instructions to obtain the headers or, review them. The first thing we will do is double-click on the e-mail message (below demonstrates an e-mail received):
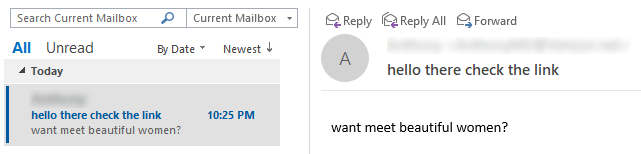
Once the e-mail message has been opened in it's own respective window as shown below we can continue to the next steps:
Now we will click on "File" menu, and then in the center search for "Properties" as shown in the animated graphic below:
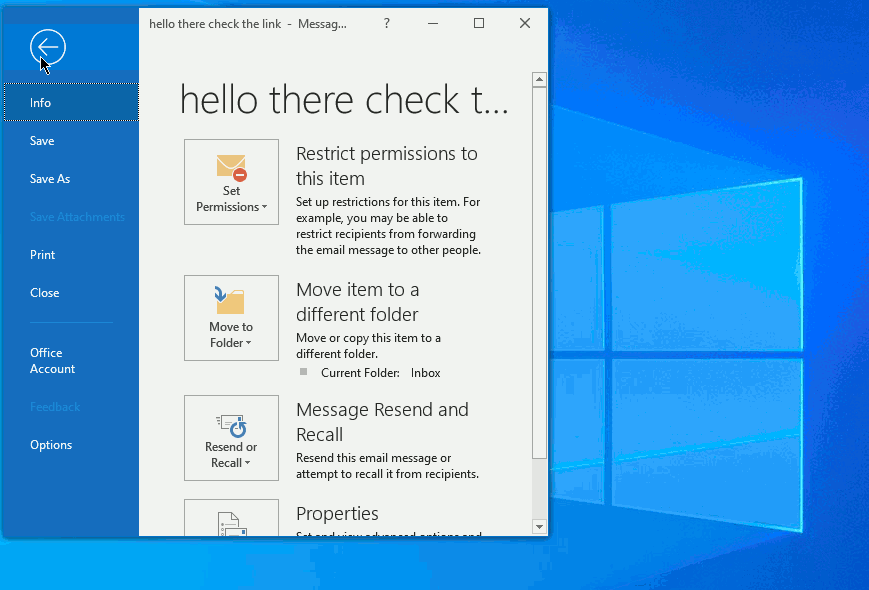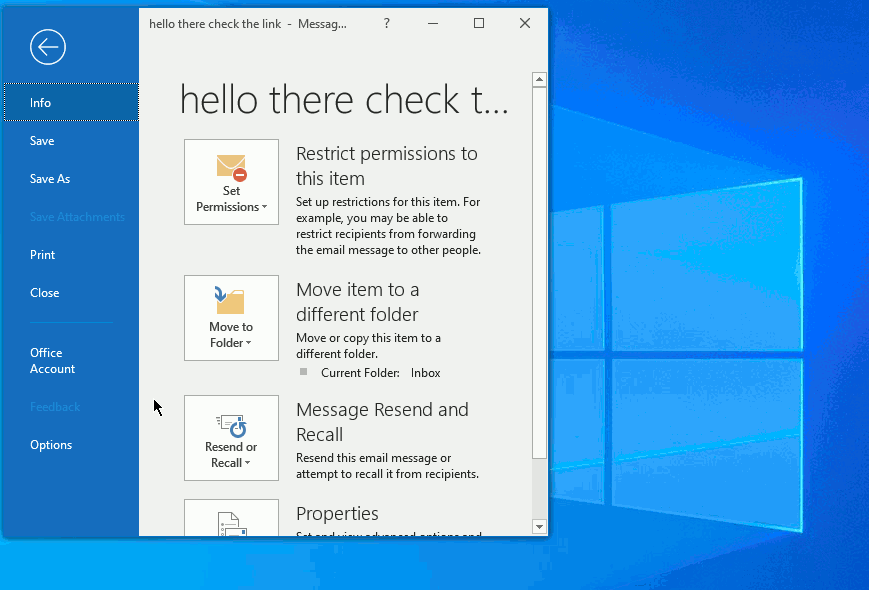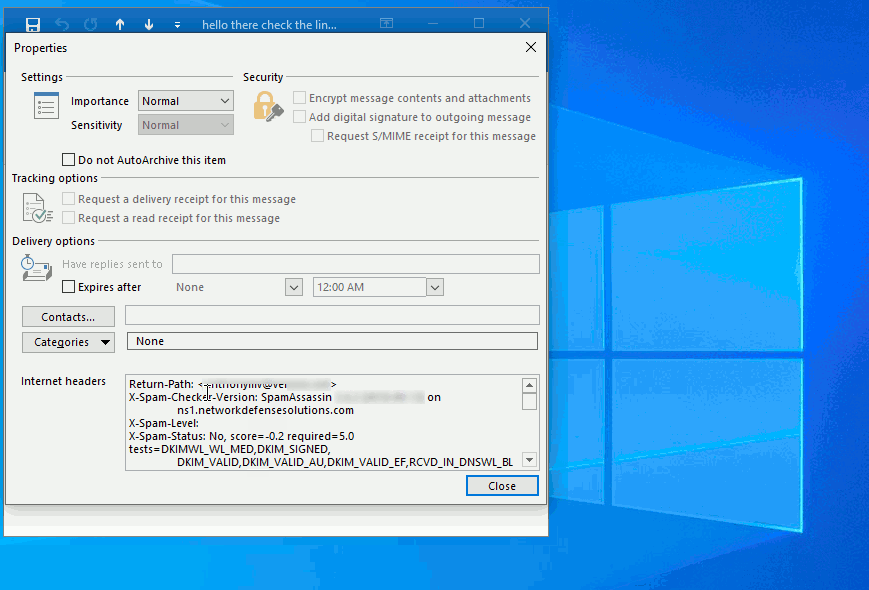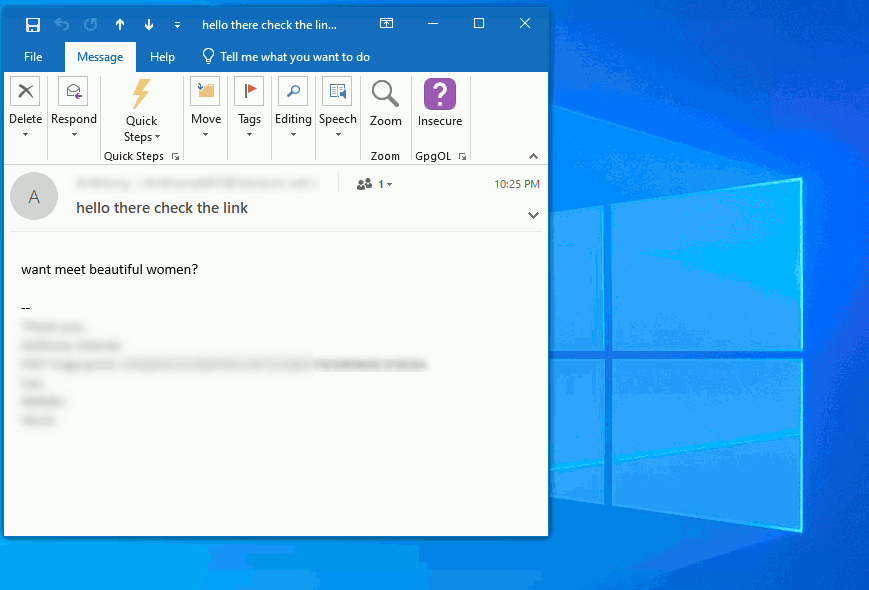
Now that you have the e-mail headers you can move forward to processing them within the application.
Ideally, you can also export the message from the in box directly to a file like we did within the thunderbird example. Simply click and hold down on the left mouse button and drag out the message to the desktop (you can also attach the file into an e-mail and send it for analysis if you have this capability. We will demonstrate both methods below:
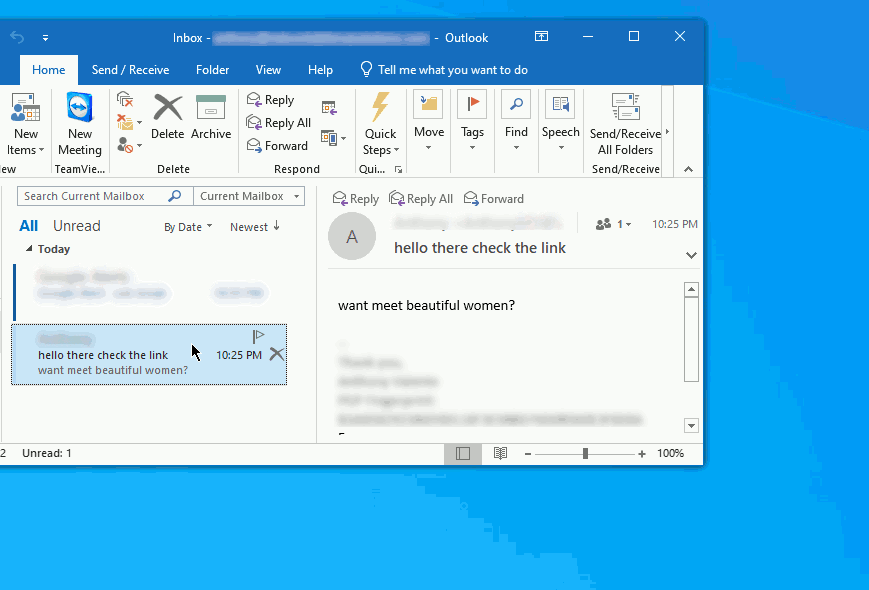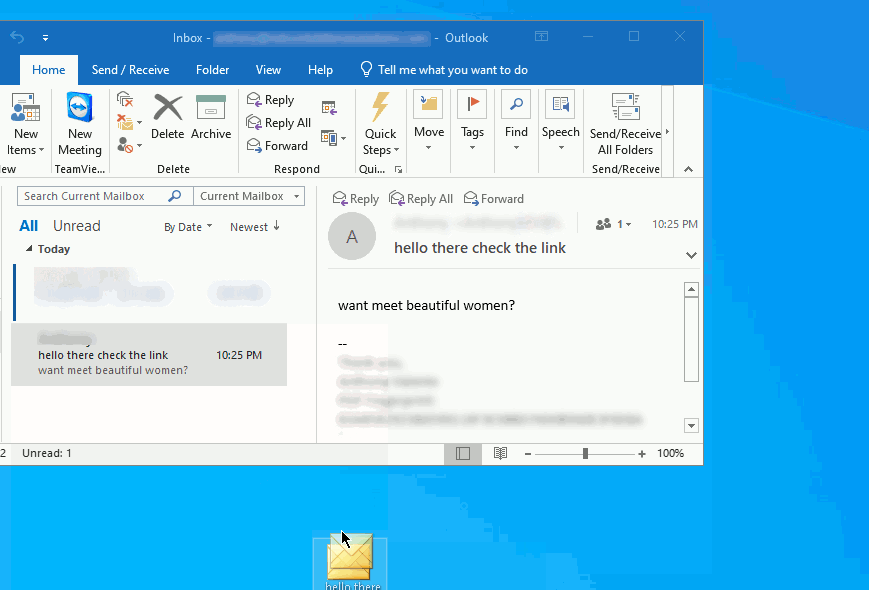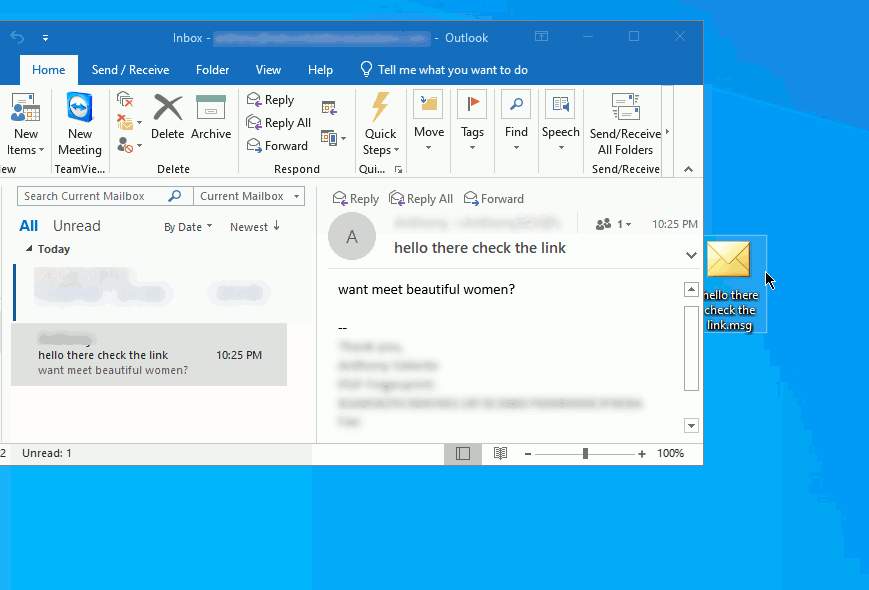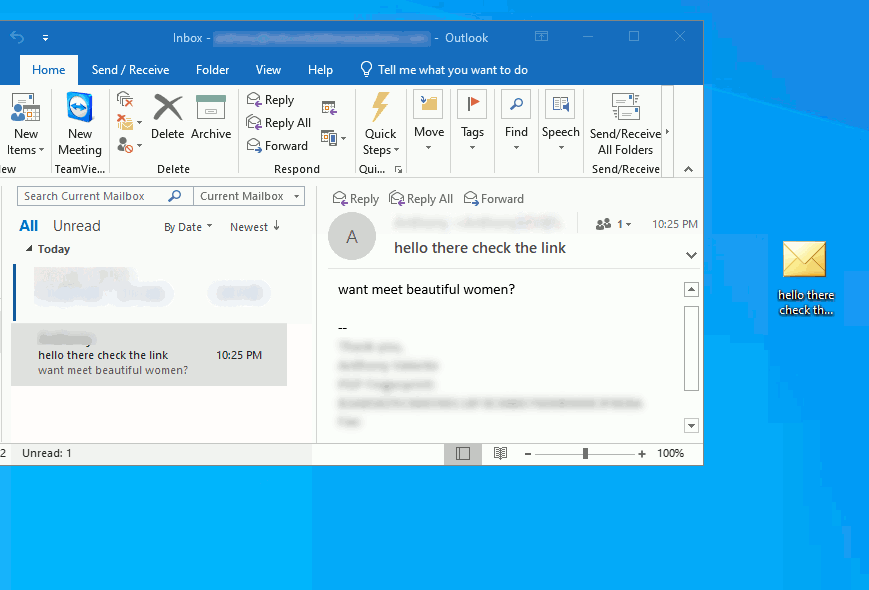
Once you have dragged the message to a location where you can easily access the file, you can simply drag and drop it back into a new e-mail and forward it to the dept. or, the location that is managing your phishing and malware e-mails.